Relevant Permissions for Accessing DynamoDB Table
Question
A team has developed an application that works with a DynamoDB table.
Now the application is going to be hosted on an EC2 Instance.
Which of the following would you implement to ensure that the application has the relevant permissions to access the DynamoDB table?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - C.
This is also given in the AWS documentation.
Options A and B are incorrect since you need to use IAM Roles.
Option D is incorrect because embedding Access keys is not a secure way to access AWS resources from EC2 Instances.
For more information on managing ID's in IAM, please refer to the below URL-
https://docs.aws.amazon.com/IAM/latest/UserGuide/id.html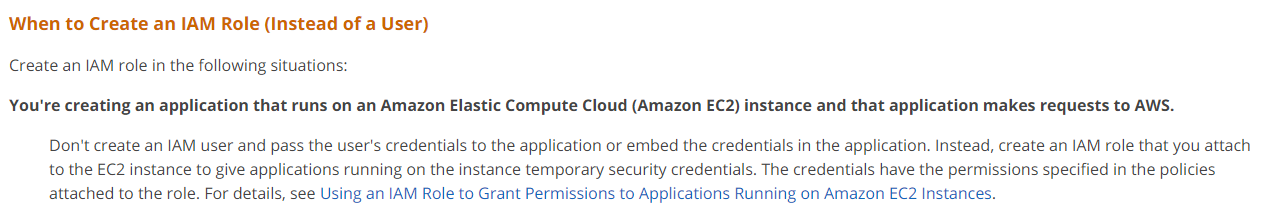
To ensure that an application hosted on an EC2 instance can access a DynamoDB table, you would need to create an IAM Role with the required permissions and assign the Role to the EC2 Instance.
An IAM Role is an AWS Identity and Access Management (IAM) entity that defines a set of permissions for making AWS service requests. It does not have any credentials that can be used to log in to an AWS account or to authenticate with AWS services. Instead, an IAM Role is assumed by a trusted entity, such as an EC2 Instance, that needs to access AWS resources.
By assigning an IAM Role to an EC2 Instance, you can grant the application running on the instance access to the DynamoDB table without needing to embed access keys or credentials in the application code. This helps to improve security and avoid exposing sensitive credentials.
Therefore, option C is the correct answer: Create an IAM Role with the required permissions and ensure that the Role is assigned to the EC2 Instance.
Option A, creating an IAM user, would not be appropriate in this scenario as IAM users are intended for human users rather than applications. Option B, creating an IAM group, would also not be appropriate as IAM groups are simply a way to group IAM users together and assign them common permissions. Option D, creating access keys, is not recommended as it would require embedding sensitive credentials in the application code, which could pose a security risk.
