Important Steps for Federated Authentication Setup between AWS and On-premises Active Directory
Question
You are working for a company and have been allocated to ensure that there is a federated authentication mechanism setup between AWS and their On-premises Active Directory.
Which of the following are important steps that need to be covered in this process? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A and D.
The AWS Documentation mentions some key aspects with regards to the configuration of On-premises AD with AWS.
Active Directory Configuration:
Determining how you will create and delineate your AD groups and IAM roles in AWS is crucial to how you secure access to your account and manage resources.
SAML assertions to the AWS environment and the respective IAM role access will be managed through regular expression (regex) matching between your on-premises AD group name to an AWS IAM role.
One approach for creating the AD groups that uniquely identify the AWS IAM role mapping is by selecting a common group naming convention.
For example, your AD groups would start with an identifier, for example, AWS-, as this will distinguish your AWS groups from others within the organization.
Next, include the 12-digit AWS account number.
Finally, add the matching role name within the AWS account.
Here is an example:
Active Directory Federation Services Configuration:
ADFS federation occurs with the participation of two parties; the identity or claims provider (in this case the owner of the identity repository - Active Directory) and the relying party, which is another application that wishes to outsource authentication to the identity provider; in this case Amazon Secure Token Service (STS)
The relying party is a federation partner that is represented by a claims provider trust in the federation service.
Option B is incorrect because the AD group name should not be matched to an IAM Group.
Option C is incorrect because the relying party should be configured in Active Directory Federation services.
For more information on the federated access, please visit the following URL:
https://aws.amazon.com/blogs/security/aws-federated-authentication-with-active-directory-federation-services-ad-fs/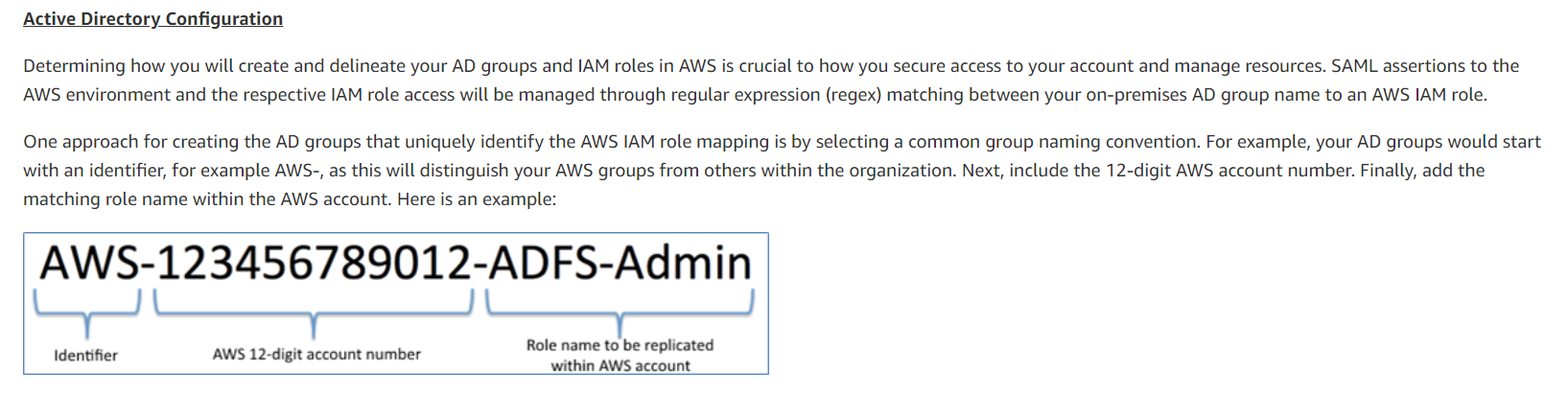
The task at hand is to set up federated authentication between an on-premises Active Directory (AD) and AWS. This will enable users in the on-premises AD to access AWS resources without the need for separate AWS IAM user accounts.
The two important steps that need to be covered in this process are:
B. Configure a proper regular expression (regex) matching between the on-premises AD group name and an AWS IAM Group. D. Configure AWS as the relying party in Active Directory Federation services.
Explanation:
B. Configure a proper regular expression (regex) matching between the on-premises AD group name and an AWS IAM Group:
In this step, a regular expression (regex) needs to be created to match the names of the on-premises AD groups with the names of the AWS IAM groups. The purpose of this is to ensure that users who are members of a particular AD group are assigned to the corresponding IAM group in AWS, which in turn grants them the necessary permissions to access AWS resources.
For example, if there is an AD group named "SalesTeam" that needs access to AWS resources, an IAM group with the same name needs to be created in AWS, and the regular expression should be configured to match the names of these groups.
D. Configure AWS as the relying party in Active Directory Federation services:
In this step, Active Directory Federation Services (AD FS) needs to be configured as the Identity Provider (IdP) to provide SAML-based authentication to AWS. This involves setting up a trust relationship between AD FS and AWS, where AD FS acts as the IdP and AWS as the Service Provider (SP).
To set up this trust relationship, AWS needs to be configured as the relying party in AD FS. This involves creating a new relying party trust in AD FS and configuring it with the necessary information, such as the SAML metadata provided by AWS.
Once these two steps are completed, users in the on-premises AD can authenticate to AWS using their AD credentials and access AWS resources based on their assigned IAM roles and permissions.