Configure Trusted Entity Principal for IAM Role in AWS
Question
One of your customers owns a SAML 2.0 Active Directory Federation Services (ADFS) server.
The customer wants to enable the federated users to access the AWS Management Console.
In order to configure it, you are creating an IAM role that identifies the IdP server for purposes of the federation.
How would you configure the trusted entity principal of the IAM role?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer: D.
Options A, B, C are incorrect because the principal should be the SAML provider in IAM.
The IAM role will establish a trust relationship between IAM and the IdP.
An example of the trust policy is as follows:
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Principal": {"Federated": "arn:aws:iam::ACCOUNT-ID-EXAMPLE:saml-provider/MyOrgSSOProvider"},
"Action": "sts:AssumeRoleWithSAML",
"Condition": {"StringEquals": {
"saml:edupersonorgdn": "MyOrg",
"saml:aud": "https://signin.aws.amazon.com/saml"
}}
}]
}
Option D is CORRECT because the IAM SAML provider should be set as the IAM principal.
To enable federated access, you should first create a SAML provider in AWS console (IAM > Identity providers > Create Identity Provider) as follows:
Reference:
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_enable-console-saml.html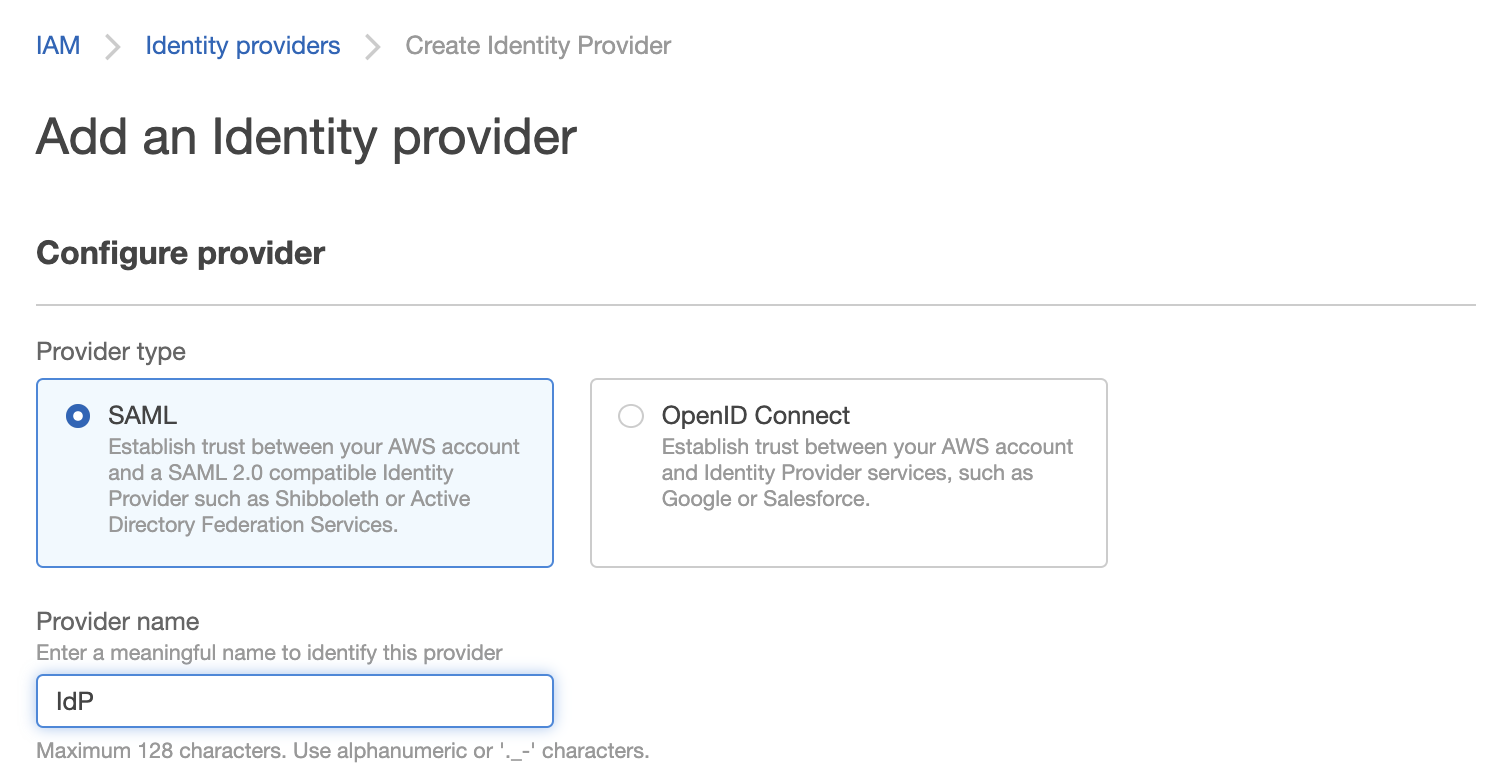
To enable the federated users to access the AWS Management Console using a SAML 2.0 Active Directory Federation Services (ADFS) server, you need to create an IAM role that identifies the IdP server for purposes of the federation. When creating the IAM role, you also need to configure the trusted entity principal, which is the entity that is trusted to make requests to assume the role.
Out of the given options, the correct answer for the trusted entity principal of the IAM role is option C: "https://signin.aws.amazon.com/saml".
Here's why:
Option A: The metadata document name of the IdP should not be the trusted entity principal of the IAM role because it is not an entity that is trusted to make requests to assume the role.
Option B: Other IAM role ARNs that the federated users will assume should not be the trusted entity principal of the IAM role because they are not entities that are trusted to make requests to assume the role.
Option C: "https://signin.aws.amazon.com/saml" should be the trusted entity principal of the IAM role because it is the entity that is trusted to make requests to assume the role when users access the AWS Management Console through the SAML 2.0 IdP. This is the URL of the AWS SAML endpoint that receives SAML assertions from the IdP.
Option D: The IAM SAML provider that you created for the IdP should not be the trusted entity principal of the IAM role because it is not an entity that is trusted to make requests to assume the role. The IAM SAML provider is used to establish trust between AWS and the IdP and is not directly involved in the federation process.
In summary, when configuring the trusted entity principal of an IAM role for federated access to the AWS Management Console using SAML 2.0 ADFS, you should set it to "https://signin.aws.amazon.com/saml".