Cloudfront Encryption
Question
You've developed an application that is going to be hosted on an EC2 Instance.
The company has decided to use Cloudfront to distribute the content.
The IT Security department has mandated that the traffic is encrypted between Cloudfront and the Viewer and Cloudfront and its origin.
How can you achieve this? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - C and D.
This is given in the AWS Documentation.
Since this is clearly given in the documentation, all other options are incorrect.
For more information on configuring HTTPS between the Viewer and Cloudfront and the Origin and Cloudfront, please refer to the below URLs-
https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/using-https-viewers-to-cloudfront.html https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/using-https-cloudfront-to-custom-origin.html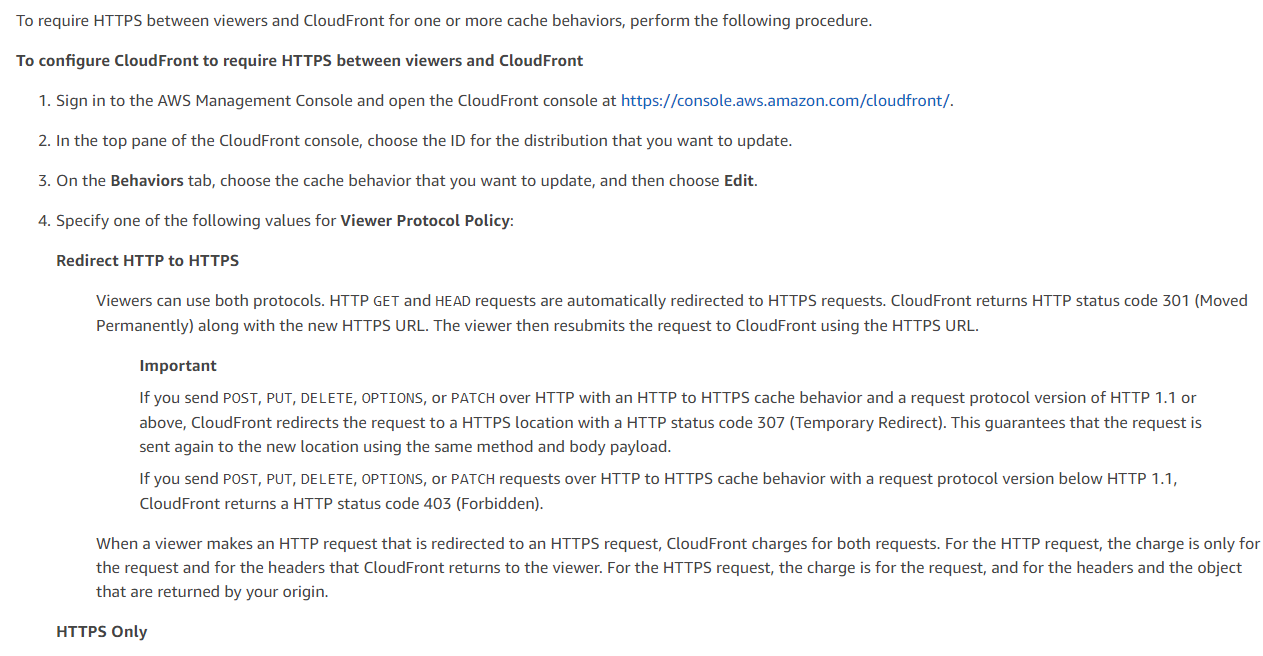
To encrypt the traffic between CloudFront and the Viewer and CloudFront and its origin, you can follow these steps:
Ensure that the Viewer Protocol policy is set to HTTPS only or Redirect HTTP to HTTPS. The Viewer Protocol Policy specifies the protocols that CloudFront will use to communicate with viewers. By setting this policy to HTTPS only or redirecting HTTP to HTTPS, you will ensure that all traffic between the viewer and CloudFront is encrypted.
Ensure that the Origin Protocol policy is set to HTTPS only. The Origin Protocol Policy specifies the protocols that CloudFront will use to communicate with your origin. By setting this policy to HTTPS only, you will ensure that all traffic between CloudFront and your origin is encrypted.
So, by configuring the Viewer Protocol Policy to use HTTPS only or redirect HTTP to HTTPS and setting the Origin Protocol Policy to HTTPS only, you will ensure that all traffic between CloudFront and the viewer and between CloudFront and the origin is encrypted.
Option A is incorrect because HTTP cannot be mapped to port 443. Port 443 is used for HTTPS traffic.
Option B is also incorrect because KMS keys are not directly related to encrypting traffic between CloudFront and the viewer or CloudFront and its origin. KMS keys are used for data encryption at rest.
Therefore, the correct answers are C and D.
