Best Practices for Securely Interacting with AWS Services using SDKs
Question
You've just started developing an application on your On-premise network.
This application will interact with the Simple Storage Service and some DynamoDB tables.
As the developer, how would you ensure that your SDK can interact with the AWS services on the cloud in the most secure manner?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - B.
An IAM role can be created to ensure the SDK can interact with AWS services on the cloud.
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_use-resources.htmlOption A is incorrect because an on-premise workstation should not use IAM Roles.
Option C is incorrect because IAM User should not be used in this scenario because the question is asking for the most secure option here.
Option D is incorrect since we should not generate a security token to interact with the various AWS services during the development phase.
For more information on the usage of credentials in AWS, please refer to the below link-
https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html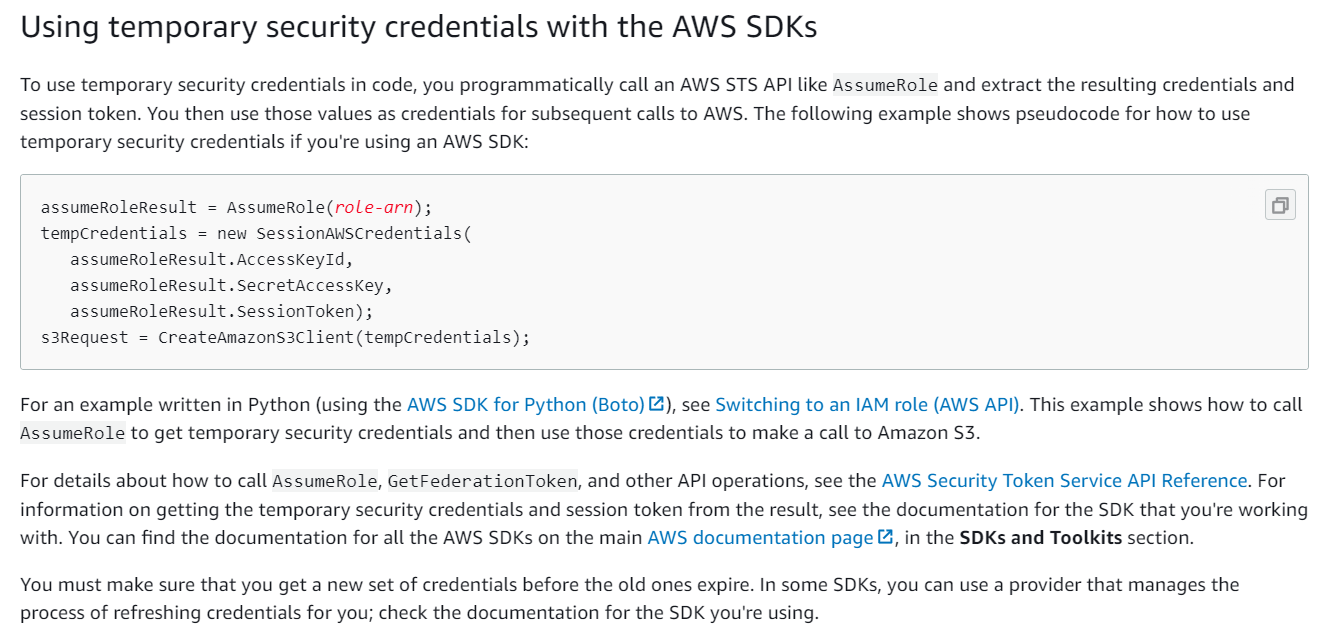
As a developer, you can ensure that your SDK interacts with AWS services in a secure manner by using the AWS Identity and Access Management (IAM) service. IAM enables you to create and manage AWS users, groups, and roles and define their permissions to access AWS resources.
Option A: Creating an IAM Role with the required permissions and adding it to your workstation is not recommended as it could compromise the security of your AWS account.
Option B: Creating an IAM Role with the required permissions and making a call to the Security Token Service (STS) is a better approach. STS provides temporary security credentials that you can use to access AWS resources. You can assume an IAM Role and obtain temporary security credentials to interact with AWS services. By using STS, you can reduce the risk of exposing long-term access keys, which can be easily compromised.
Option C: Creating an IAM User and generating access keys, then using them from within your program is also not recommended as the access keys can be easily compromised. It is recommended to use IAM Roles and temporary security credentials to access AWS resources instead of IAM Users and long-term access keys.
Option D: Creating an IAM User, generating a security token, and using the Security Token from within your program is not a recommended approach as it requires you to manage the security token, which can be a cumbersome process. It is recommended to use STS to obtain temporary security credentials instead.
Therefore, the correct answer is B. Create an IAM Role with the required permissions and make a call to the STS service.