Question 37 of 115 from exam AZ-304: Microsoft Azure Architect Design
Question
HOTSPOT -
You have five .NET Core applications that run on 10 Azure virtual machines in the same subscription.
You need to recommend a solution to ensure that the applications can authenticate by using the same Azure Active Directory (Azure AD) identity. The solution must meet the following requirements:
-> Ensure that the applications can authenticate only when running on the 10 virtual machines.
-> Minimize administrative effort.
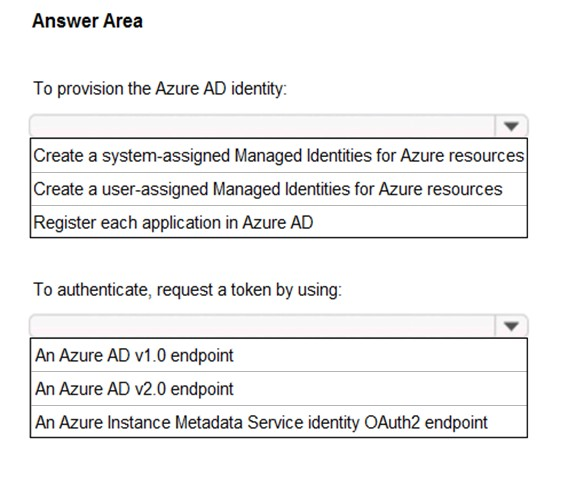
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
Hot Area:
Explanations
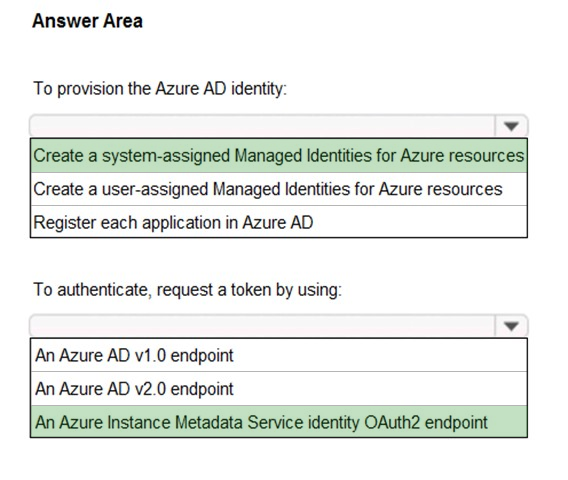
Box 1: Create a system-assigned Managed Identities for Azure resource
The managed identities for Azure resources feature in Azure Active Directory (Azure AD) feature provides Azure services with an automatically managed identity in Azure AD. You can use the identity to authenticate to any service that supports Azure AD authentication, including Key Vault, without any credentials in your code.
A system-assigned managed identity is enabled directly on an Azure service instance. When the identity is enabled, Azure creates an identity for the instance in the Azure AD tenant that's trusted by the subscription of the instance. After the identity is created, the credentials are provisioned onto the instance.
Box 2: An Azure Instance Metadata Service Identity
See step 3 and 5 below.
How a system-assigned managed identity works with an Azure VM
1. Azure Resource Manager receives a request to enable the system-assigned managed identity on a VM.
2. Azure Resource Manager creates a service principal in Azure AD for the identity of the VM. The service principal is created in the Azure AD tenant that's trusted by the subscription.
3. Azure Resource Manager configures the identity on the VM by updating the Azure Instance Metadata Service identity endpoint with the service principal client
ID and certificate.
4. After the VM has an identity, use the service principal information to grant the VM access to Azure resources. To call Azure Resource Manager, use role-based access control (RBAC) in Azure AD to assign the appropriate role to the VM service principal. To call Key Vault, grant your code access to the specific secret or key in Key Vault.
5. Your code that's running on the VM can request a token from the Azure Instance Metadata service endpoint, accessible only from within the VM
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/overview