Question 21 of 236 from exam AZ-500: Microsoft Azure Security Technologies
Question
HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
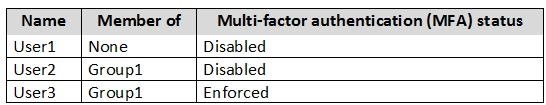
Azure AD Privileged Identity Management (PIM) is enabled for the tenant.
In PIM, the Password Administrator role has the following settings:
-> Maximum activation duration (hours): 2
-> Send email notifying admins of activation: Disable
-> Require incident/request ticket number during activation: Disable
-> Require Azure Multi-Factor Authentication for activation: Enable
Require approval to activate this role: Enable

-> Selected approver: Group1
You assign users the Password Administrator role as shown in the following table.
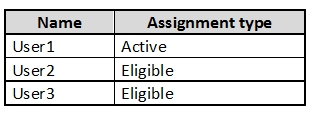
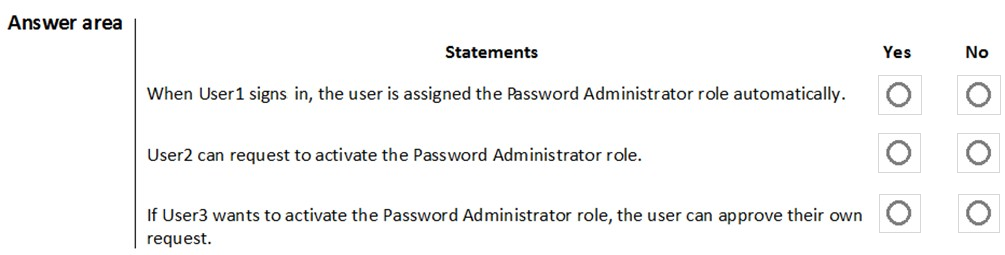
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Explanations
Box 1: Yes -
Active assignments don't require the member to perform any action to use the role. Members assigned as active have the privileges assigned to the role at all times.
Box 2: No -
MFA is disabled for User2 and the setting Require Azure Multi-Factor Authentication for activation is enabled.
Note: Eligible assignments require the member of the role to perform an action to use the role. Actions might include performing a multi-factor authentication
(MFA) check, providing a business justification, or requesting approval from designated approvers.
Box 3: Yes -
User3 is Group1, which is a Selected Approver Group
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-resource-roles-assign-roles