Question 116 of 236 from exam AZ-500: Microsoft Azure Security Technologies
Question
HOTSPOT -
You have the Azure virtual networks shown in the following table.
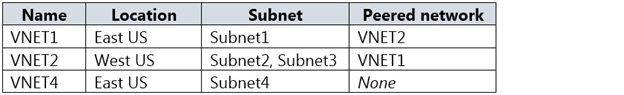
You have the Azure virtual machines shown in the following table.
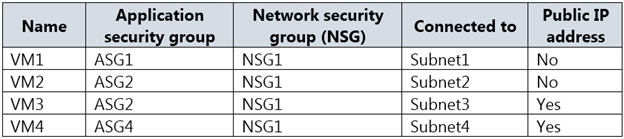
The firewalls on all the virtual machines allow ping traffic.
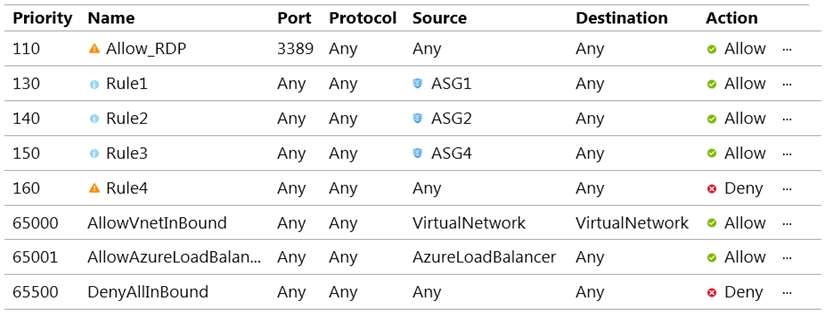
NSG1 is configured as shown in the following exhibit.
Inbound security rules -
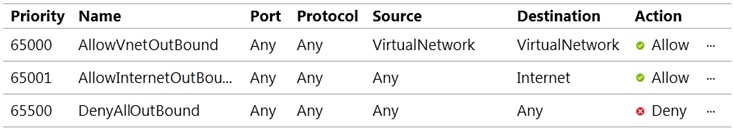
Outbound security rules -
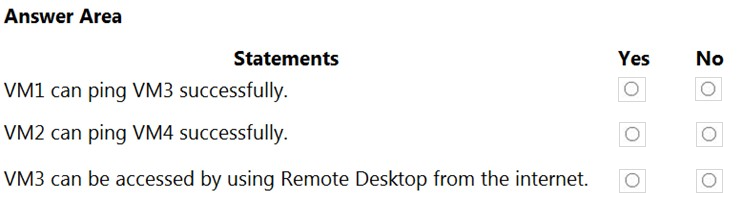
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Explanations
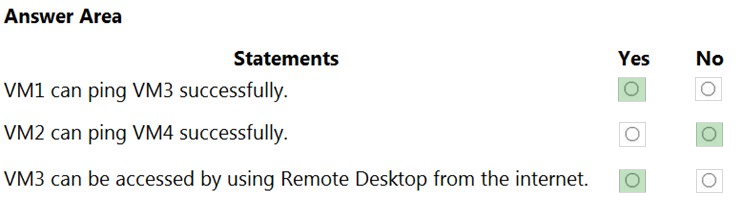
Box 1: Yes -
VM1 and VM3 are on peered VNets. The firewall rules with a source of ASG1 and ASG2 allow 'any' traffic on 'any' protocol so pings are allowed between VM1 and VM3.
Box 2: No -
VM2 and VM4 are on separate VNets and the VNets are not peered. Therefore, the pings would have to go over the Internet. VM4 does have a public IP and the firewall allows pings. However, for VM2 to be able to ping VM4, VM2 would also need a public IP address. In Azure, pings don't go out through the default gateway as they would in a physical network. For an Azure VM to ping external IPs, the VM must have a public IP address assigned to it.
Box 3: Yes -
VM3 has a public IP address and the firewall allows traffic on port 3389.
Manage security operations
