Question 172 of 236 from exam AZ-500: Microsoft Azure Security Technologies
Question
DRAG DROP -
You have an Azure subscription that contains 100 virtual machines. Azure Diagnostics is enabled on all the virtual machines.
You are planning the monitoring of Azure services in the subscription.
You need to retrieve the following details:
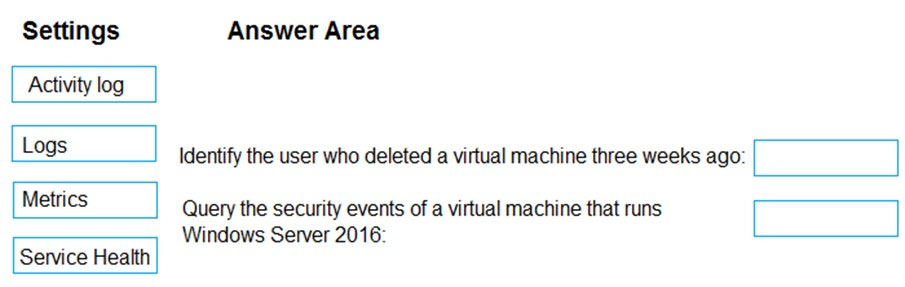
-> Identify the user who deleted a virtual machine three weeks ago.
-> Query the security events of a virtual machine that runs Windows Server 2016.
What should you use in Azure Monitor? To answer, drag the appropriate configuration settings to the correct details. Each configuration setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Explanations
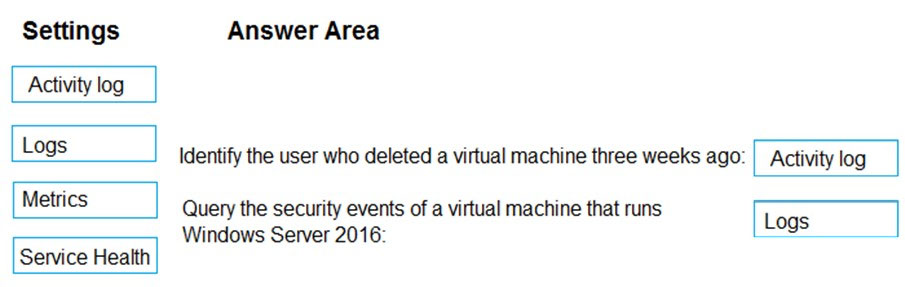
Box1: Activity log -
Azure activity logs provide insight into the operations that were performed on resources in your subscription. Activity logs were previously known as audit logs or
operational logs, because they report control-plane events for your subscriptions.
Activity logs help you determine the what, who, and when for write operations (that is, PUT, POST, or DELETE).
Box 2: Logs -
Log Integration collects Azure diagnostics from your Windows virtual machines, Azure activity logs, Azure Security Center alerts, and Azure resource provider logs. This integration provides a unified dashboard for all your assets, whether they're on-premises or in the cloud, so that you can aggregate, correlate, analyze, and alert for security events.
https://docs.microsoft.com/en-us/azure/security/azure-log-audit