Ensure Secure Access to DynamoDB from EC2 Instances in Private Subnet | AWS Exam Prep
Question
There is a set of EC2 Instances in a private subnet.
The application hosted on these EC2 Instances needs to access a DynamoDB table running on AWS.
It needs to be ensured that traffic does not flow out to the internet.
How can this be achieved?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: A.
Option A is CORRECT because a VPC endpoint for DynamoDB enables Amazon EC2 instances in your VPC to use their private IP addresses to access DynamoDB with no exposure to the public internet.
Your EC2 instances do not require public IP addresses, and you don't need an internet gateway, a NAT device, or a virtual private gateway in your VPC.Option B is incorrect because a VPN connection is used for establishing connectivity between an on-premises environment and AWS Cloud Platform.
Option C is incorrect because using a NAT gateway will allow the EC2 machine to reach the public internet.
This would not restrict access to DynamoDB within the AWS network.
Option D is incorrect because VPC Peering is used to connect multiple VPCs together.
This would not allow connecting EC2 with DynamoDB within the same VPC over the AWS network.
The following diagram from the AWS Documentation shows how you can access the DynamoDB service from within a VPC without going to the Internet.
For more information on VPC endpoints for DynamoDB, kindly refer to the following URL:
https://docs.aws.amazon.com/amazondynamodb/latest/developerguide/vpc-endpoints-dynamodb.html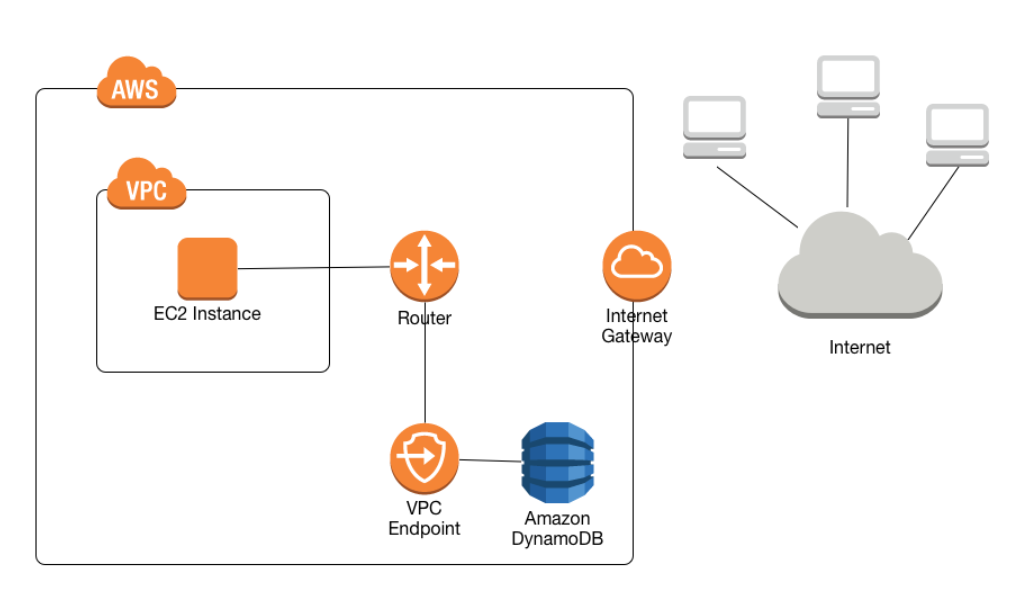
To ensure that the traffic from the EC2 Instances in a private subnet does not flow out to the internet while allowing the application to access a DynamoDB table running on AWS, the best solution is to use a VPC endpoint for DynamoDB.
Explanation:
A Virtual Private Cloud (VPC) is an isolated network within the AWS cloud environment. It allows customers to launch AWS resources in a private, isolated virtual network, which provides additional security by restricting access to those resources.
In this scenario, the EC2 instances are in a private subnet, which means they are not directly accessible from the internet. However, to access DynamoDB, the instances need to communicate with the DynamoDB endpoint, which is a public AWS service.
To prevent the traffic from the EC2 instances from flowing out to the internet, we need to use a VPC endpoint. A VPC endpoint allows you to privately connect your VPC to supported AWS services without requiring an internet gateway, NAT device, VPN connection, or firewall proxy.
Using a VPC endpoint for DynamoDB allows the EC2 instances in the private subnet to connect to the DynamoDB endpoint directly, without the traffic leaving the VPC. This ensures that the traffic does not flow out to the internet and remains within the private network.
Option B, using a VPN connection from the VPC, would provide a secure connection between the VPC and the on-premises network or another VPC, but it is not required for accessing DynamoDB.
Option C, using a NAT gateway from the VPC, would allow instances in the private subnet to access the internet, but it is not needed in this scenario, where the goal is to restrict access to the internet.
Option D, using a VPC peering connection to the DynamoDB table, is not possible since DynamoDB is a service and not a VPC. Peering connections are established between VPCs.
In summary, the best solution to ensure that traffic does not flow out to the internet while allowing the EC2 instances in a private subnet to access a DynamoDB table running on AWS is to use a VPC endpoint for DynamoDB.
