Ensure Policy Compliance: Encrypting Objects in Your S3 Bucket
Question
A company is storing sensitive data in their S3 bucket.
The company policy states that all objects in the S3 bucket need to be encrypted at rest.
Which of the following helps ensure this policy is met?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A.
This is also given in the AWS Documentation.
Option B is incorrect as it denies the upload if the header includes x-amz-server-side-encryption.
Option C and D are incorrect because there is no such header as x-allow-encryption.
For more information on Server-Side Encryption, please refer to the below URL-
https://docs.aws.amazon.com/AmazonS3/latest/dev/UsingServerSideEncryption.html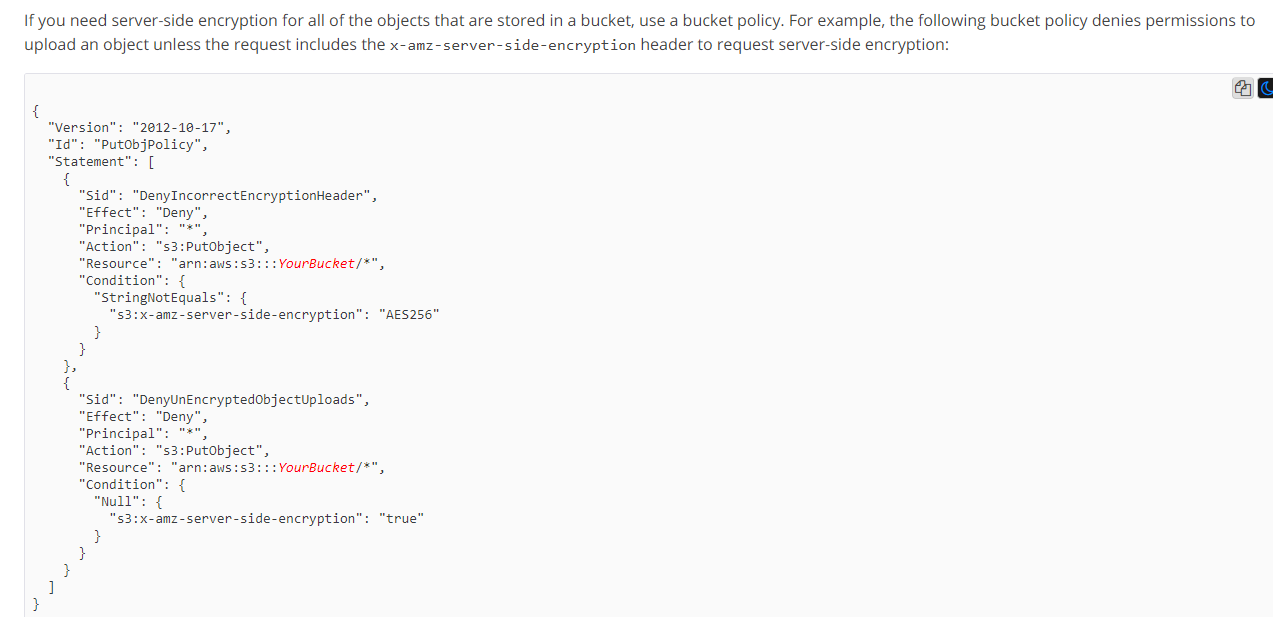
The correct answer is A. Deny permission to upload an object if the header does not include x-amz-server-side-encryption.
Explanation: Amazon S3 provides server-side encryption (SSE) to encrypt data at rest. SSE encrypts the data as it is being uploaded to S3, and decrypts the data when it is being downloaded from S3. Amazon S3 SSE provides three options for managing keys: SSE-S3, SSE-KMS, and SSE-C.
To enforce a policy that requires all objects in the S3 bucket to be encrypted at rest, you can use a Bucket Policy or an IAM Policy that denies permission to upload objects that are not encrypted at rest. The correct way to do this is by using the "x-amz-server-side-encryption" header.
If you want to enforce that all objects in a bucket are encrypted at rest using SSE-S3, you can use the following Bucket Policy:
json{ "Version":"2012-10-17", "Statement":[ { "Sid":"RequireServerSideEncryption", "Effect":"Deny", "Principal":"*", "Action":"s3:PutObject", "Resource":"arn:aws:s3:::examplebucket/*", "Condition":{ "StringNotEquals":{ "s3:x-amz-server-side-encryption":"AES256" } } } ] } This policy denies permission to upload an object if the header does not include x-amz-server-side-encryption with the value AES256, which means the object must be encrypted at rest using SSE-S3.
Option B is incorrect because it denies permission to upload an object if the header includes x-amz-server-side-encryption. This would prevent users from uploading encrypted objects, which is not what the policy requires.
Option C and D are incorrect because they use a custom header "x-allow-encryption", which is not a valid S3 header for SSE.