Ways to Ensure Data Security with AWS Elastic Load Balancer
Question
Which of the following are ways to ensure that data is secured while in transit when using the AWS Elastic load balancer? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - B and D.
The AWS documentation mentions the following.
You can create a load balancer that uses the SSL/TLS protocol for encrypted connections (also known as SSL offload)
This feature enables traffic encryption between your load balancer and the clients that initiate HTTPS sessions, and for connections between your load balancer and your EC2 instances.
For more information on Elastic Load balancer and secure listeners, please refer to the below link:
http://docs.aws.amazon.com/elasticloadbalancing/latest/classic/elb-https-load-balancers.htmlNote:
AS per AWS documentation,
If you use HTTPS or SSL for your front-end connections, you must deploy an X.509 certificate (SSL server certificate) on your load balancer.
The load balancer decrypts requests from clients before sending them to the back-end instances (known as SSL termination)
If you don't want the load balancer to handle the SSL termination (known as SSL offloading), you can use TCP for both the front-end and back-end connections, and deploy certificates on the registered instances handling requests.
For more details, please check below AWS Docs:
https://docs.aws.amazon.com/elasticloadbalancing/latest/classic/elb-listener-config.html https://docs.aws.amazon.com/elasticloadbalancing/latest/classic/using-elb-listenerconfig-quickref.html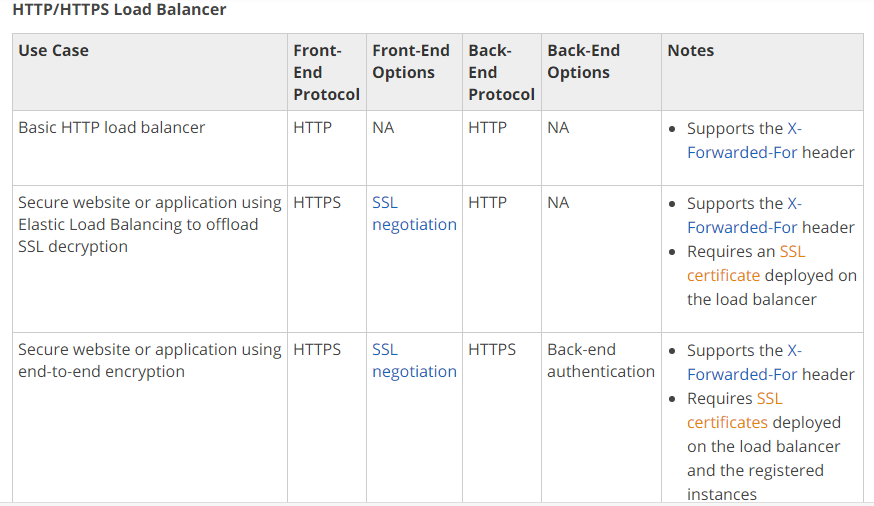
When using the AWS Elastic Load Balancer (ELB), there are multiple options to secure data in transit between the client and the ELB. Two of these options are:
- Use an SSL/TLS front-end listener for your ELB
- Use an HTTPS front-end listener for your ELB
Explanation:
Use an SSL/TLS front-end listener for your ELB: This option uses SSL (Secure Sockets Layer) or TLS (Transport Layer Security) to encrypt data in transit between the client and the ELB. SSL/TLS front-end listener can be configured on the ELB using an SSL certificate. When a client connects to the ELB, the client and the ELB negotiate the encryption algorithm and create a secure tunnel between them. This ensures that the data transmitted between the client and the ELB is encrypted and secure.
Use an HTTPS front-end listener for your ELB: HTTPS (Hypertext Transfer Protocol Secure) is an extension of HTTP that uses SSL/TLS to encrypt data in transit. When a client connects to an ELB with an HTTPS front-end listener, the client and ELB negotiate a secure tunnel using SSL/TLS encryption. This option ensures that the data transmitted between the client and the ELB is encrypted and secure.
Therefore, options B and D are correct as both options provide encryption and secure data transmission. Option A and C are not correct since they do not provide encryption for data in transit.
In conclusion, using an SSL/TLS or HTTPS front-end listener on your ELB will ensure that data is secured while in transit between the client and the ELB.