Connecting AWS Lambda Function to RDS Instance for MySQL Details Configuration
Question
You are setting up AWS Lambda function to receive messages from SQS queue, process the message body and insert one record in MySQL RDS instance.
You have setup SQS event trigger as AWS Lambda function.
However, for connecting to RDS instance, you need MySQL details such as hostname, username and password.
Where would you configure them?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: B.
https://docs.aws.amazon.com/lambda/latest/dg/env_variables.html?shortFooter=true.
Option A is not correct.
The statement is true, however the encryption only happens after deployment of lambda function.
Option C is not a valid statement.
Option D looks correct.
However, out of given options, Option B is more valid and recommended.
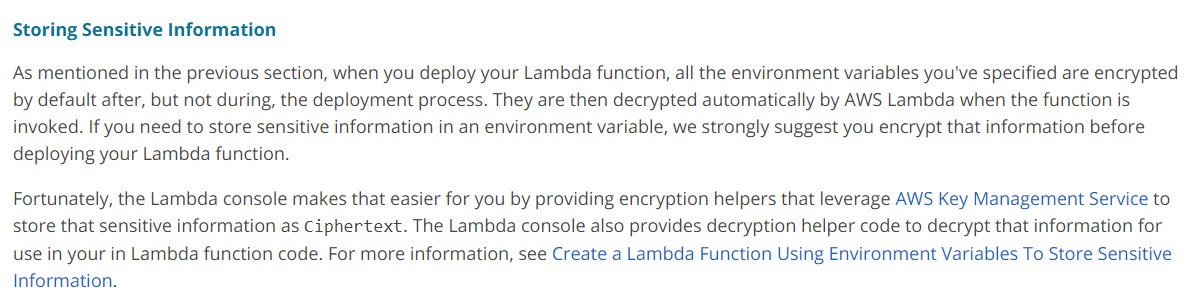
When setting up an AWS Lambda function to receive messages from an SQS queue, process the message body, and insert a record in MySQL RDS instance, you will need MySQL details such as hostname, username, and password to connect to the RDS instance. There are various ways to configure these details securely.
Option A suggests using environment variables to pass configuration. AWS Lambda supports environment variables that can be used to pass configuration values to your function. These environment variables are automatically encrypted by AWS default KMS keys and decrypted when used in the Lambda function. This approach ensures that sensitive information is kept secure, and you don't have to worry about encrypting and decrypting data manually.
Option B also suggests using environment variables to pass configuration, but this time, it recommends using encryption helpers to encrypt sensitive information by your own KMS key. You can then decrypt the variable using decryption helper code provided in the console. This approach gives you more control over the encryption of sensitive data, but it requires more effort to set up.
Option C suggests using properties files in AWS Lambda function for any such configuration. Properties files are plain text files that contain key-value pairs of configuration values. These files can be encrypted by AWS in transit and at rest, ensuring that sensitive data is kept secure. This approach is similar to using environment variables, but it requires creating and managing properties files, which can be cumbersome.
Option D suggests storing configuration details in an S3 bucket and enabling encryption on the S3 bucket. You can then perform S3 get object to get the configuration details in the Lambda function code. This approach gives you the flexibility to store configuration data separately from the Lambda function code, but it requires additional permissions to access the S3 bucket and retrieve the configuration details.
In summary, Option A and Option B are both viable solutions to configure MySQL details securely when setting up an AWS Lambda function to receive messages from an SQS queue, process the message body, and insert a record in MySQL RDS instance. Option C and Option D are also possible but require more effort to set up and manage.