Viable Techniques to Mitigate DDoS Attacks
Question
You are designing a social media site and are considering how to mitigate distributed denial-of-service (DDoS) attacks.
Which of the below are viable mitigation techniques? Choose 3 answers from the options below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E. F.Answer - C,D and E.
The below snapshot from the AWS documentation shows the best architecture practises for avoiding DDos attacks.
For best practises against DDos attacks , please visit the below link:
https://d0.awsstatic.com/whitepapers/DDoS_White_Paper_June2015.pdf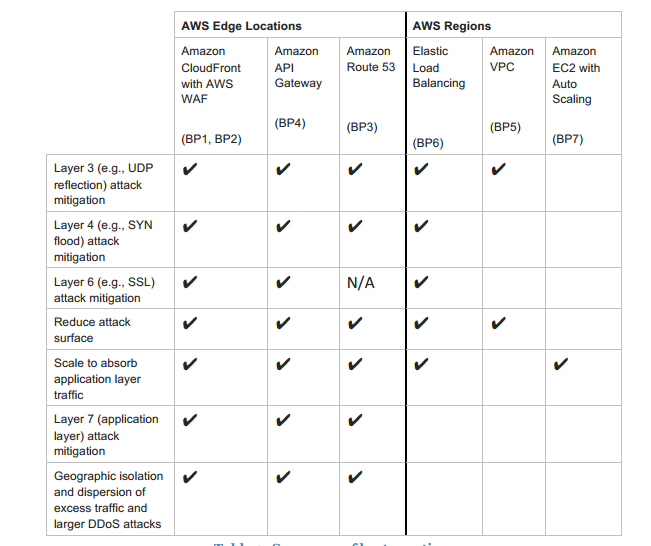
Distributed denial-of-service (DDoS) attacks can cause a significant amount of damage to any website or application, particularly those that depend on social media. DDoS attacks can lead to service disruption, causing loss of revenue, reputation damage, and decreased user experience. As such, it is crucial to have effective mitigation techniques in place to prevent such attacks. Below are the viable mitigation techniques:
A. Add multiple elastic network interfaces (ENIs) to each EC2 instance to increase the network bandwidth: By adding multiple ENIs to each EC2 instance, you can increase the available network bandwidth. This technique helps to absorb the traffic generated during a DDoS attack, thus reducing the impact of the attack. Additionally, this technique can help in ensuring that the application continues to function even during peak traffic times.
C. Use an Amazon CloudFront distribution ( WAF enabled ) for both static and dynamic content: Amazon CloudFront is a content delivery network (CDN) service that can help mitigate DDoS attacks by distributing the incoming traffic across multiple regions. This technique can help absorb the attack traffic by distributing the load and providing the necessary capacity to handle the increased traffic. Additionally, by enabling the WAF (Web Application Firewall) feature, CloudFront can detect and block malicious traffic before it reaches the origin server.
D. Use an Elastic Load Balancer with auto-scaling groups at the web application tier and Route53 with a routing policy (like "weighted routing policy") for the EC2 instances: An Elastic Load Balancer (ELB) can distribute traffic evenly across multiple EC2 instances, which can help absorb the traffic generated during a DDoS attack. By using auto-scaling groups, you can add more EC2 instances to the group when traffic levels increase. This ensures that the application remains available during peak traffic times. Additionally, by using Route53 with a routing policy, you can distribute traffic across multiple regions and redirect traffic away from regions that are experiencing high traffic levels or under attack.
In conclusion, it is essential to have a combination of multiple mitigation techniques in place to ensure that your social media site is protected from DDoS attacks. These techniques can help absorb and distribute the traffic, and detect and block malicious traffic before it reaches the origin server.