Integrating Single Sign-On for Amazon S3 Storage with Corporate AD/LDAP Directory
Question
Your fortune 500 company has undertaken a TCO analysis evaluating the use of Amazon S3 versus acquiring more hardware.
The outcome was that all employees would be granted access to use Amazon S3 for storage of their personal documents.
Which of the following will you need to consider so that you can set up a solution that incorporates a single sign-on from your corporate AD or LDAP directory?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Answer - A, B, and D.
In questions like this where an application or user needs to be given access using Single Sign On (SSO), the following steps are very important.
(i) setting up an identity provider for federated access.
(ii) authenticating users using corporate data store or active directory-user-attributes.
(iii) getting temporary access tokens/credentials using AWS STS.
(iv) creating the IAM Role that has access to the needed AWS Resources.
Option A is CORRECT because as mentioned above, setting up an identity provider for federated access is needed.
Option B is CORRECT because as mentioned above, getting temporary access tokens/credentials using AWS STS is needed.
Option C is incorrect because tagging each folder in a bucket does not help in this scenario.
Option D is CORRECT because as mentioned above, creating the IAM Role that has access to the needed AWS Resources is needed.
Option E is incorrect because you should be creating IAM Roles rather than IAM Users.
The diagram below showcases how authentication is carried out when having an identity broker.
This is an example of a SAML connection, but the same concept holds true for getting access to an AWS resource.
For more information on federated access, please visit the below link-
http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_common-scenarios_federated-users.html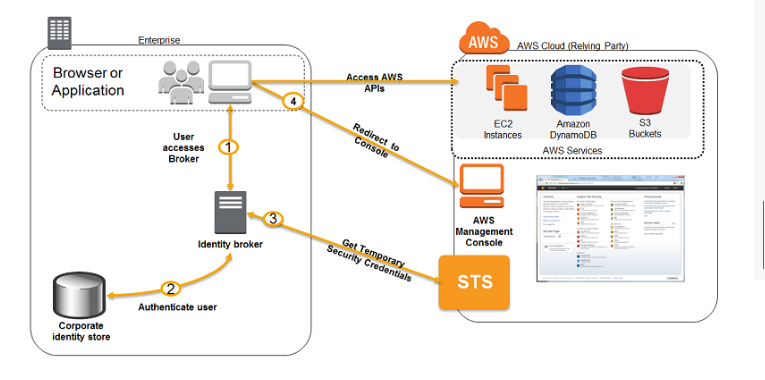
To enable single sign-on (SSO) for your corporate Active Directory (AD) or LDAP directory users, you will need to set up a federation proxy or identity provider. This will allow your users to authenticate once with their corporate credentials and then be granted access to Amazon S3.
Answer A is correct: Setting up a federation proxy or identity provider is the correct approach to enable SSO from your corporate AD or LDAP directory to Amazon S3. A federation proxy acts as a mediator between your corporate directory and AWS, while an identity provider is a service that authenticates users and provides temporary security credentials to access AWS resources.
Answer B is not correct: Using AWS Security Token Service (STS) to generate temporary tokens is a method of enabling cross-account access or allowing users to assume temporary roles in your AWS account. It is not related to setting up SSO with your corporate directory.
Answer C is not correct: Tagging each folder in the bucket is a method of organizing and categorizing objects in Amazon S3, but it is not related to enabling SSO with your corporate directory.
Answer D is not complete: Configuring IAM roles with suitable permissions is a crucial step in granting access to AWS resources, including Amazon S3. However, it is not sufficient to enable SSO with your corporate directory. You will need to set up a federation proxy or identity provider to authenticate your users with their corporate credentials.
Answer E is not correct: Setting up a matching IAM user for every user in your corporate directory is not a scalable or secure approach. IAM users are intended for managing access to AWS resources within your own account, not for authenticating external users. Additionally, creating and managing a large number of IAM users can be time-consuming and error-prone.
In summary, the correct answer is A: Setting up a federation proxy or identity provider is necessary to enable SSO with your corporate AD or LDAP directory. This will allow your users to authenticate once with their corporate credentials and then be granted access to Amazon S3.
