Resolve VPC Peering Connection Issues
Question
You've set up a VPC peering connection between 2 VPCs, VPC A and VPC B.
You are trying to ping the Instances in each VPC to each other.
But you are not able to do so.
You have verified the Security Groups for the Instances and the NACLs and confirmed that ICMP traffic is allowed.
What steps need to be taken to resolve the issue? Choose 2 answers from the options below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A and C.
Options B and D are incorrect since the traffic should not move through the Internet gateway.
The AWS Documentation mentions the following to support this.
Route Tables for a VPC Peering Connection.
A VPC peering connection is a networking connection between two VPCs that allows you to route traffic between them using private IPv4 addresses.
Instances in either VPC can communicate with each other as if they are part of the same network.
To enable the routing of traffic between VPCs in a VPC peering connection, you must add a route to one or more of your VPC route tables that points to the VPC peering connection to access all or part of the CIDR block of the other VPC in the peering connection.
Similarly, the owner of the other VPC must add a route to their VPC route table to route traffic back to your VPC.For example, you have a VPC peering connection (pcx-1a2b1a2b) between two VPCs, with the following information.
VPC A: vpc-1111aaaa, CIDR block is 10.0.0.0/16
VPC B: vpc-2222bbbb, CIDR block is 172.31.0.0/16
To enable traffic between the VPCs and allow access to the entire IPv4 CIDR block of either VPC, the VPC A route table is configured as follows.
For more information on Route Tables for VPC Peering connections, please refer to the below URL.
https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_Route_Tables.html#route-tables-vpc-peering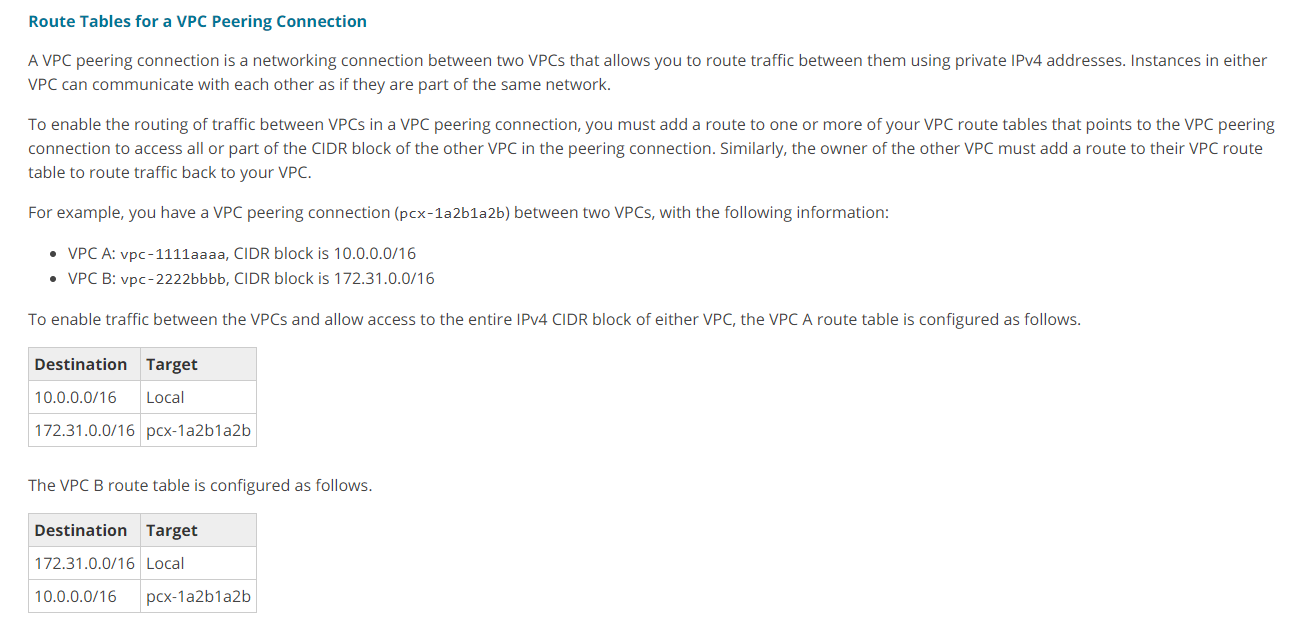
To resolve the issue of not being able to ping instances in each VPC after setting up a VPC peering connection, there are two steps you can take:
- Add a route in the route table in VPC A to VPC B via the VPC peering connection.
- Add a route in the route table in VPC B to VPC A via the VPC peering connection.
Explanation:
When a VPC peering connection is established between two VPCs, the route tables of each VPC need to be updated to allow traffic to flow between the two VPCs. By default, the route table of a VPC only contains a local route for its own CIDR block.
Therefore, to allow traffic to flow between the two VPCs, a route needs to be added in each VPC's route table to point to the other VPC's CIDR block via the VPC peering connection.
Option A - Add a route in the route table in VPC A to VPC B via the VPC peering connection: This step adds a route in the route table of VPC A to point to the CIDR block of VPC B via the VPC peering connection. This allows traffic to flow from VPC A to VPC B.
Option C - Add a route in the route table in VPC B to VPC A via the VPC peering connection: This step adds a route in the route table of VPC B to point to the CIDR block of VPC A via the VPC peering connection. This allows traffic to flow from VPC B to VPC A.
Options B and D are incorrect because adding a route via the Internet gateway will not allow traffic to flow between the two VPCs. The Internet gateway is only used for traffic going to and from the internet.
In summary, to allow traffic to flow between two VPCs after setting up a VPC peering connection, you need to add a route in each VPC's route table to point to the other VPC's CIDR block via the VPC peering connection.