Considerations for VPC Design
Question
Your architecture team has recommended the following for the VPCs in your AWS Account. · A shared services VPC which would provide services to other VPCs · A hosted VPC that will be accessible to the customer · The hosted VPC will also interact with the shared services VPC.Which of the following should also be considered as part of the design? Choose 3 answers from the options given below.
Each answer is an independent design solution.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Answer - A, B and C.
One option is to create an AWS PrivateLink that can access the services in the AWS shared VPC.
You can create your own application in your VPC and configure it as an AWS PrivateLink-powered service (referred to as an endpoint service)
Other AWS principals can create a connection from their VPC to your endpoint service using an interface VPC endpoint.
You are the service provider, and the AWS principals that create connections to your service are service consumers.
And the other option is to make the VPC public.
But the right security measures need to be put in place.
Option B is correct because, in VPC peering, it states that, You may want to use this spoke configuration when you have resources on a central VPC, such as a repository of services, that other VPCs need to access.
The other VPCs do not need access to each others' resources.
They only need access to resources on the central VPC.
Option D is incorrect because this option should only be used for a transit VPC.For more information on VPC and Subnet sizing, please visit the below URL:
https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/endpoint-service.html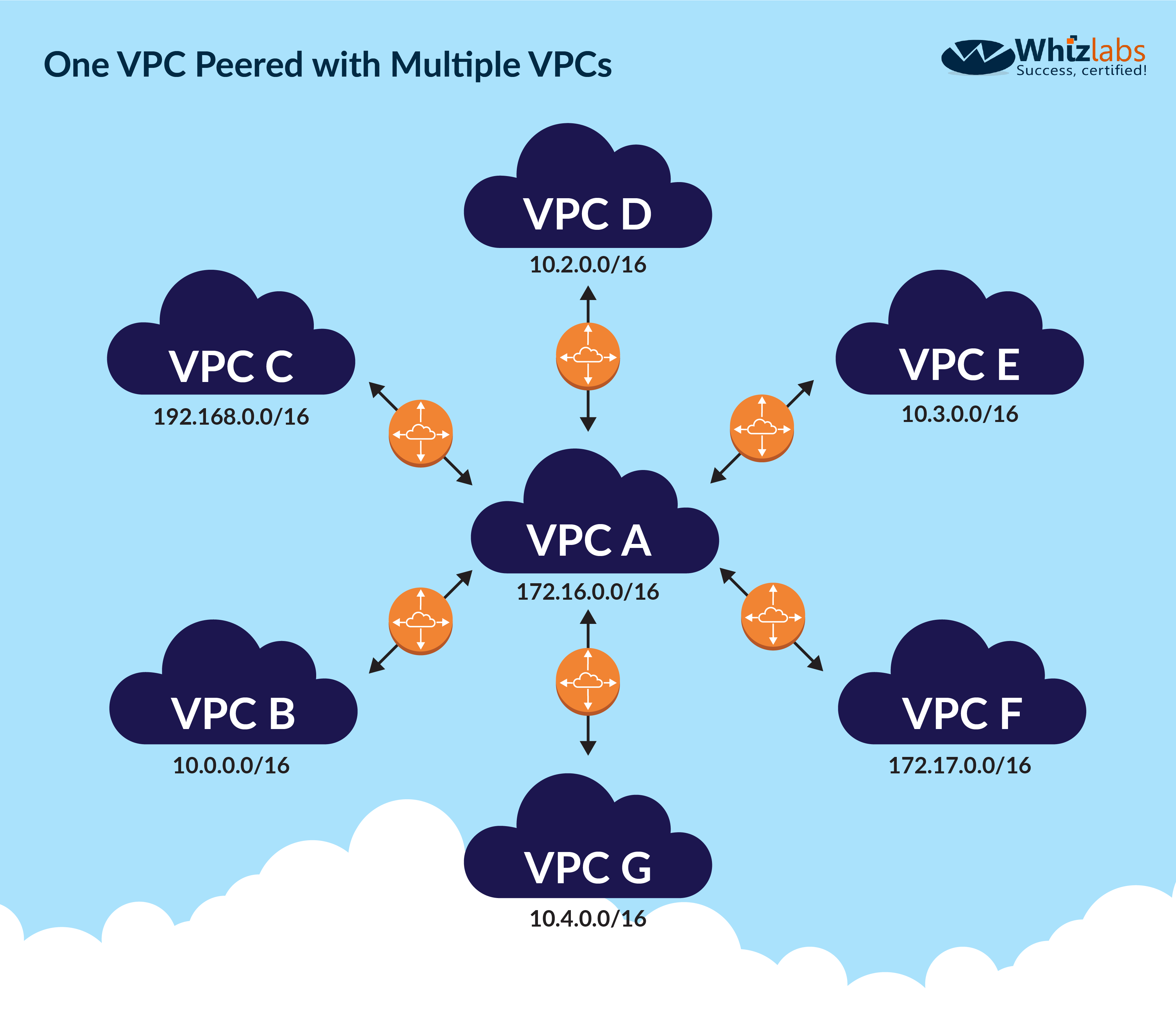
The scenario presented in the question involves three VPCs, a shared services VPC, a hosted VPC accessible to customers, and interaction between the two. The question requires identifying three independent design solutions that should also be considered as part of the design.
Here are the explanations for each option:
A. Ensure an AWS PrivateLink is available for accessing the Shared services VPC:
AWS PrivateLink provides private connectivity between VPCs and AWS services without the need for a public IP address, NAT, or VPN connection. With PrivateLink, the shared services VPC can expose its services to other VPCs privately, without exposing them to the Internet. This solution is ideal for security and compliance reasons, and it can help simplify network architecture by reducing the number of network hops between VPCs.
B. Use VPC peering between the shared services VPC and other VPCs:
VPC peering is a way to connect two VPCs together so that they can communicate directly over the Amazon network. By using VPC peering, the shared services VPC can communicate with other VPCs as if they were part of the same network. This solution is ideal for scenarios where multiple VPCs need to communicate with each other frequently.
C. Setup communication via the Public IPs (or via the Internet) and ensure the right security measures are in place for inter-VPC communications:
This option involves setting up public IPs or using the Internet to communicate between the shared services VPC and other VPCs. However, this solution can be less secure than the other options, as it exposes the VPCs to the public Internet. To ensure security, the right security measures must be in place, such as encryption, firewalls, and access controls.
D. Create a VPN between each VPC:
This option involves creating a VPN connection between the shared services VPC and other VPCs. A VPN connection provides a secure and private connection between VPCs over the Internet. However, this option can be more complex to set up and maintain, and it may not be the best solution if frequent communication is required between VPCs.
E. Ensure the Virtual private gateway is in place for the other VPCs:
A virtual private gateway is a logical entity in AWS that represents the VPN endpoint on the AWS side of a VPN connection. By ensuring the virtual private gateway is in place for other VPCs, it enables them to communicate securely with the shared services VPC over the VPN connection. However, like option D, this option may be more complex to set up and maintain.
In summary, the three independent design solutions that should be considered as part of the design are:
- Ensure an AWS PrivateLink is available for accessing the Shared services VPC.
- Use VPC peering between the shared services VPC and other VPCs.
- Setup communication via the Public IPs (or via the Internet) and ensure the right security measures are in place for inter-VPC communications.