Get Service Last Access Data for AWS Organization Entities: Effective Method
Question
You need to maintain an AWS Organization.
The Organization includes several organization units (OUs) and dozens of accounts.
You want to get the service last access data for different OUs and accounts.
Then you can refine the policies in the Organization and allow access to only the services that the entities in the AWS Organization use.
Which method would you take to address this requirement?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer - C.
Users can view service last access data for AWS Organizations through IAM console, AWS CLI or API.
Please check https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_access-advisor-view-data-orgs.html for details.
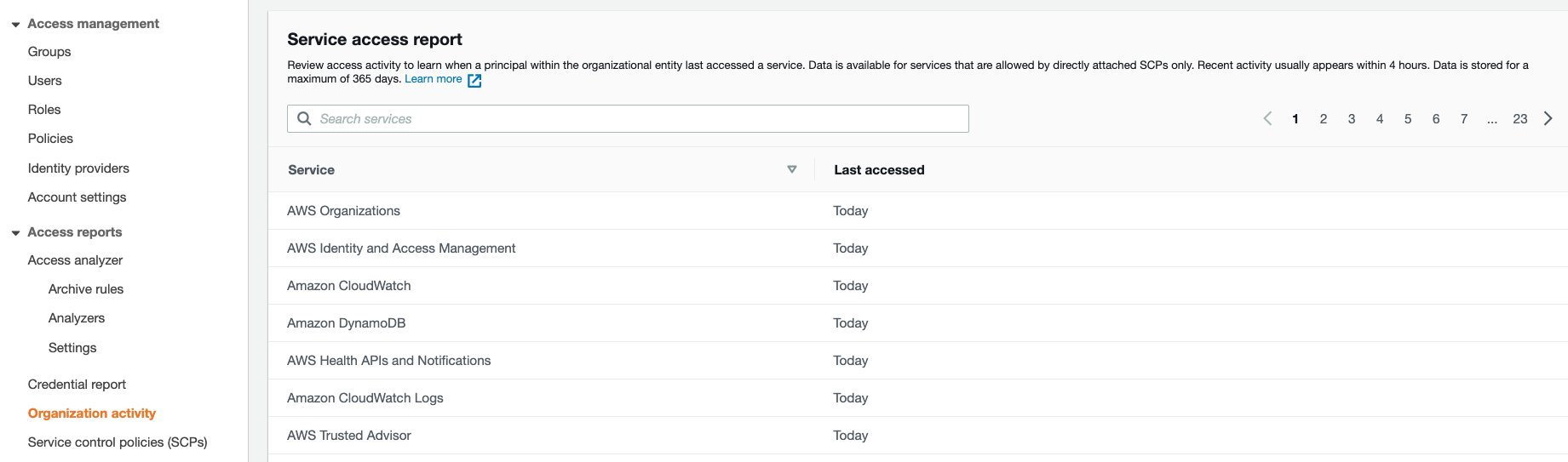
Option A is incorrect: Because the service last access data should be seen in IAM -> Access reports -> Organization activity.
The report cannot be found in AWS Organizations.
Option B is incorrect: Because the correct AWS CLI commands for Organizations should be aws iam generate-organizations-access-report and aws iam get-organizations-access-report.
Option C is CORRECT: Users can get the access report in IAM for an Organization:
Option D is incorrect: Because Resource Access Manager is used to share AWS resources with other AWS accounts.
It does not provide service access data.
To maintain an AWS Organization and refine the policies for service access, it is important to understand the last access data for different OUs and accounts. This information can be used to allow access only to the services that the entities in the AWS Organization use.
The correct method to get the service last access data for different OUs and accounts is option D, "In AWS Resource Access Manager, download the service access report for any given OU, account, or the whole AWS Organization."
AWS Resource Access Manager (RAM) is a service that enables resource sharing across AWS accounts. It allows you to share AWS resources such as Amazon Virtual Private Cloud (VPC) subnets, Amazon Elastic Block Store (EBS) volumes, and Amazon S3 buckets with other AWS accounts in your organization.
To use RAM to download the service access report, follow these steps:
Log in to the AWS Management Console and navigate to the AWS Resource Access Manager dashboard.
From the dashboard, select the "Resource shares" tab.
From the "Resource shares" tab, select the OU or account for which you want to download the service access report.
Click on the "Actions" button and select "View service last accessed data" from the dropdown menu.
RAM generates a report that shows the services that were last accessed by the selected OU or account. The report also includes information such as the date of the last access and the IAM entity that accessed the service.
Download the report to your local machine or S3 bucket for further analysis.
By using RAM to download the service access report, you can get a comprehensive view of the services that are being used by different entities in your AWS Organization. This information can be used to refine policies and allow access only to the services that are actually being used, reducing the attack surface and improving the overall security posture of your organization.
Option A is not the best choice, as it requires logging in to each entity in the AWS Console to download the access data report, which can be time-consuming and error-prone.
Option B is also not ideal, as it only provides information about a specific IAM resource (user, group, role, or policy) and not the entire Organization.
Option C is not accurate, as the service access report in IAM only provides information about the activities within IAM, and not the entire Organization.