How to Check Last Accessed Time of an IAM Policy
Question
You are a DevOps engineer and you need to clean up IAM entities that are no longer used.
There is an IAM policy called IAMAccessForDemo which contains CloudFormation full access, KMS full access and some other permissions.
However, nobody in your team knows what the IAM policy is used for and whether it is safe to delete it.
How would you check the time when the granted services by the policy were last accessed?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer - D.
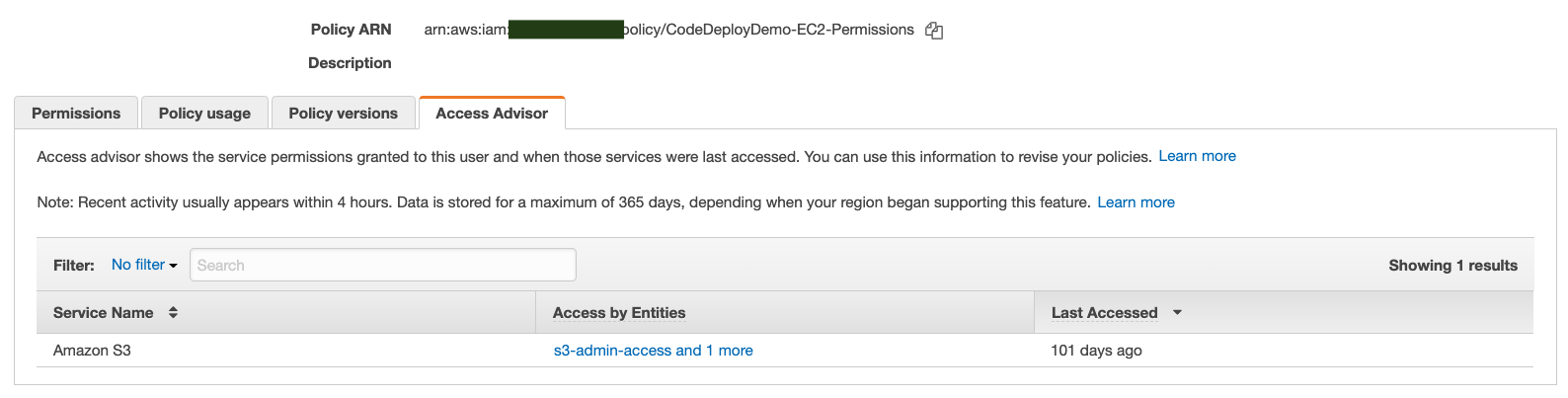
The Service Last Accessed Data can be found in IAM Access Advisor.
Check https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_access-advisor-example-scenarios.html for the example scenarios.
Option A is incorrect: The Policy usage can show whether the policy is used by other IAM entities such as IAM users.
However, it does not show the last accessed data.
Option B is incorrect: CloudTrail does not show when the services permitted by the policy were last accessed.
Besides, you can only view the last 90 days of events in CloudTrail.
Option C is incorrect: Because the configuration timeline in AWS Config does not show the last accessed data.
Option D is CORRECT: IAM Access Advisor contains the required information.
Take the below screenshot as an example:
Sure, I'd be happy to provide a detailed explanation for each option.
Option A: In AWS Console, click the IAM policy and go to the Policy usage tab. Check if the policy is assigned to any entity. If yes, do not delete the policy.
This option suggests that you check the Policy usage tab in the IAM policy in the AWS Management Console. This tab shows you which entities (e.g., users, groups, roles) have been granted the policy. If you see that the policy is still assigned to any entity, it may not be safe to delete the policy yet since it is still being used. However, note that even if a policy is not currently assigned to any entity, it may still be used in the future if an entity is created that requires the same permissions.
Option B: In the AWS CloudTrail console, search the IAM policy to see if the policy has been accessed recently.
This option suggests that you use AWS CloudTrail to check if the IAM policy has been accessed recently. AWS CloudTrail is a service that logs AWS API calls and can be used to monitor and troubleshoot AWS resources. By searching the CloudTrail logs for the IAM policy, you can see when the policy was last accessed. If the policy has not been accessed in a long time, it may be safe to delete it. However, note that just because a policy has not been accessed recently does not mean it is not being used.
Option C: Look at the IAM Policy configuration timeline in AWS Config to see if the permissions allowed by the policy have been accessed recently.
This option suggests that you use AWS Config to see when the permissions allowed by the IAM policy have been accessed. AWS Config is a service that provides a detailed view of the configuration of AWS resources over time, making it easier to audit resource configuration changes, and security compliance. By looking at the IAM Policy configuration timeline in AWS Config, you can see when the permissions allowed by the policy were last accessed. If they were not accessed in a long time, it may be safe to delete the policy. However, note that just because the permissions have not been accessed recently does not mean the policy is not being used.
Option D: In AWS Console, check the Access Advisor of the IAM policy to see when the permitted services were last accessed. If they were accessed a long time ago, it would be safe to delete the policy.
This option suggests that you use the Access Advisor feature in the IAM policy in the AWS Management Console. The Access Advisor shows you the last time a particular service or resource was accessed by any entity that has the policy attached to it. This information can help you determine if the policy is still being used. If the services and resources permitted by the policy have not been accessed in a long time, it may be safe to delete the policy. However, note that this information only shows you when the services or resources were last accessed, and not whether the policy itself is still being used.
