Securely Accessing Your S3 Bucket: AWS Certified Developer - Associate Exam Answers
Question
Your company currently has an S3 bucket hosted in an AWS Account.
It holds information that needs to be accessed by a partner account.
Which is the MOST secure way to allow the partner account to access the S3 bucket in your account? Choose 3 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A, C and D.
The below diagram from the AWS documentation showcases an example of this wherein an IAM role and external ID can access an AWS account resources.
Option B is invalid because Roles are assumed and not IAM users.
For more information on creating roles for external ID's, please visit the following URL-
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create_for-user_externalid.html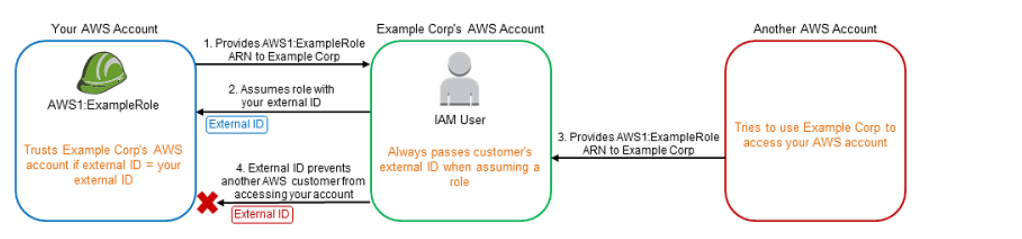
To allow a partner account to access an S3 bucket hosted in your AWS account in the most secure way, there are three options:
Create an IAM role that can be assumed by the partner account: This option allows you to create an IAM role that grants access to the S3 bucket and then allows the partner account to assume that role. This approach is preferred as it provides a higher level of security as compared to creating an IAM user with access keys. The partner account can assume the IAM role using the AWS Security Token Service (STS).
Use an external ID: When creating the IAM role, you can also specify an external ID. This external ID acts as a shared secret between your account and the partner account, and is used to prevent unauthorized access. When the partner account requests access to assume the IAM role, they must include the external ID in their request.
Provide the ARN for the role to the partner account: Once the IAM role is created, you can provide the Amazon Resource Name (ARN) for the role to the partner account. This allows the partner account to assume the role and access the S3 bucket using the AWS Management Console or SDKs.
Option B, creating an IAM user with access keys, is not recommended because access keys can be easily shared or compromised, resulting in a potential security breach.
In summary, the most secure way to allow a partner account to access an S3 bucket hosted in your AWS account is to create an IAM role that can be assumed by the partner account, use an external ID for authentication, and provide the ARN for the role to the partner account.
