Resolving Direct Requests Issue
Question
You've set up a Classic Load Balancer and EC2 Instances behind the Load Balancer.
The following Security Groups have been set. · Security Group for the ELB - Accept Incoming traffic on port 80 from 0.0.0.0/0 · Security Group for the EC2 Instances - Accept Incoming traffic on port 80 from 0.0.0.0/0 It has been noticed that the EC2 Instances are getting a large number of direct requests from the Internet.
What should be done to resolve the issue?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - B.
The AWS Documentation mentions the following for how the security groups should be defined for the underlying EC2 Instances.
Option A is incorrect since the ELB needs to accept traffic from everywhere.
Options C and D are incorrect since there is no mention in the question of HTTPS traffic.
For more information on the Security Groups for Classic Load Balancers, please refer to the below URL.
https://docs.aws.amazon.com/elasticloadbalancing/latest/classic/elb-security-groups.html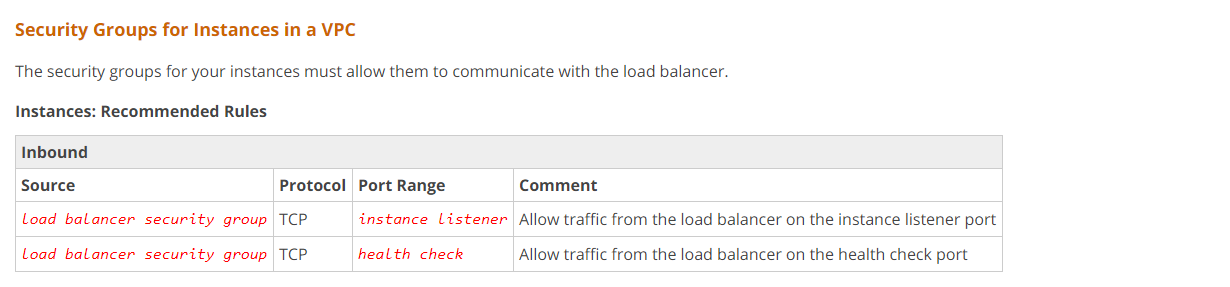
The issue here is that the EC2 instances are receiving direct requests from the Internet, which defeats the purpose of using a load balancer in the first place. The load balancer is designed to distribute traffic among the EC2 instances, improving availability, scalability, and performance.
To resolve the issue, we need to ensure that all incoming traffic is directed through the load balancer. This can be done by restricting the security groups for the ELB and the EC2 instances.
Option A suggests changing the ELB security group to only accept traffic from the EC2 instances on port 80. This would prevent any external traffic from reaching the load balancer, effectively rendering it useless.
Option B suggests changing the EC2 instance security group to only accept traffic from the ELB security group on port 80. This is the correct solution as it ensures that all incoming traffic is directed through the load balancer. By restricting access to port 80 only from the ELB security group, the EC2 instances will only accept traffic that has been forwarded by the load balancer.
Option C suggests changing the ELB security group to only accept traffic from the EC2 instances on port 443. This is not relevant to the issue at hand, as port 443 is typically used for HTTPS traffic.
Option D suggests changing the EC2 instance security group to only accept traffic from the ELB security group on port 443. This is also not relevant to the issue at hand, as port 443 is not being used by the load balancer in this scenario.
In conclusion, option B is the correct answer as it ensures that all traffic is directed through the load balancer and prevents direct requests to the EC2 instances from the Internet.
