Question 84 of 270 from exam CAS-003: CompTIA CASP+
Question
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products.
The analyst believes a malicious actor is scanning the web form.
To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control.
Given the log below:
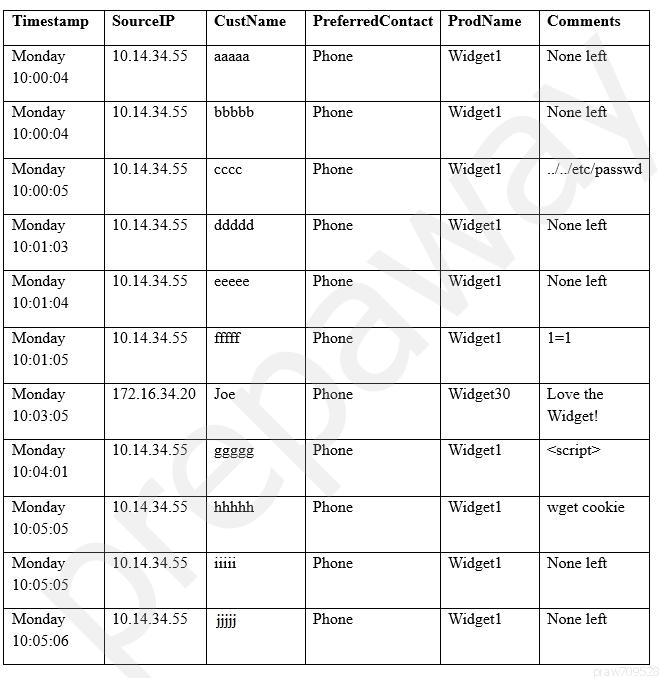
Which of the following is the MOST likely type of activity occurring?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.A.